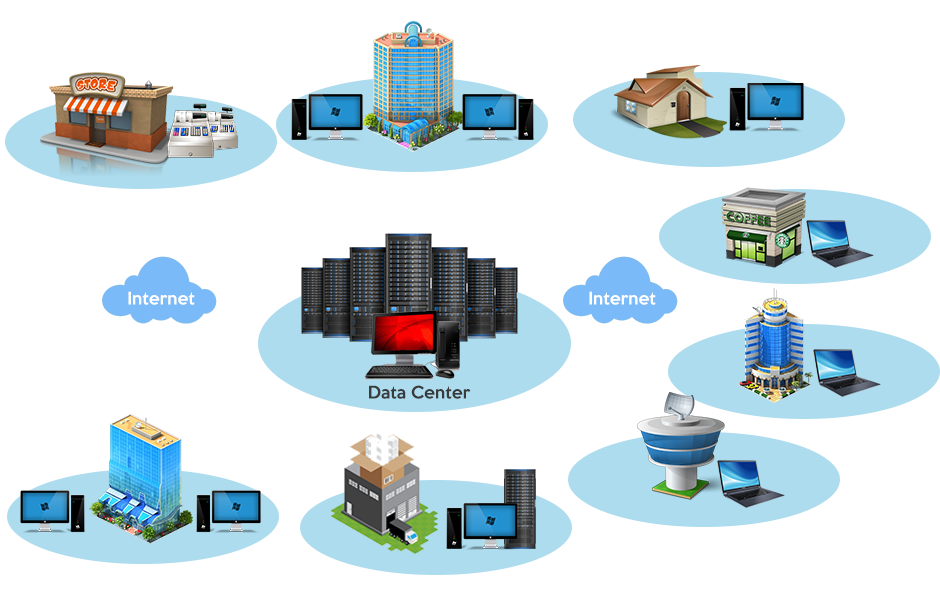
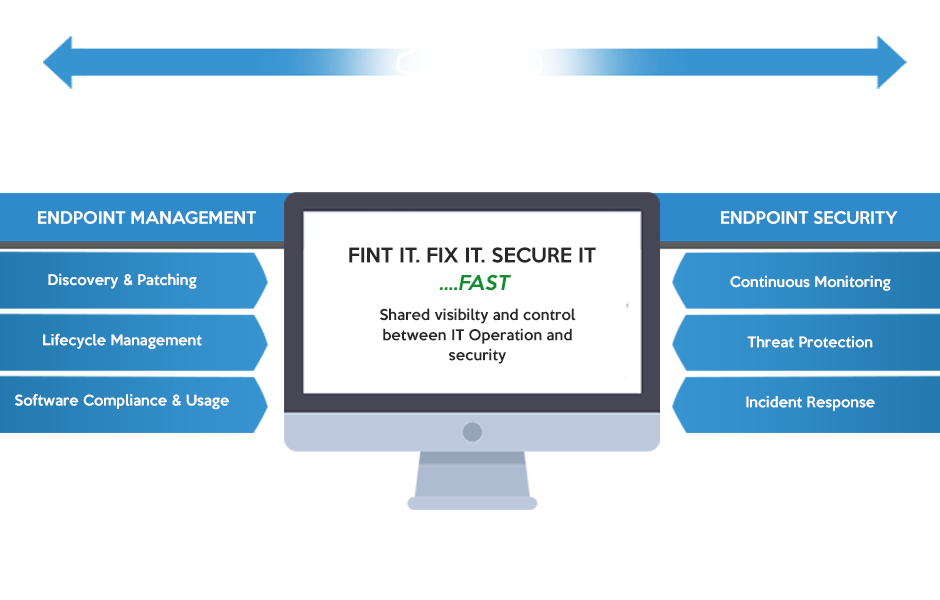
If your organization is like most, you have an ever-changing diversity of endpoints connecting to your corporate network – and among them are often non-compliant or rogue devices, over which you have no visibility or control.
BigFix secures all your endpoints from laptops, desktops, and servers to point-of-sale devices, ATMs and kiosks. It allows you to continuously monitor each endpoint for potential threats and enforce compliance with security, regulatory, and operational policies. It even works in remote locations with low or no bandwidth.
Now you can protect your network by securing and monitoring every endpoint before, during, and after an attack. With BigFix, you get real-time situational awareness and incident response across all endpoints. Because when it comes to protecting your data, minutes matter. With rapidly increasing numbers of remote workers and mobile devices, there is no well-defined perimeter. The perimeter, by necessity, must be the endpoint itself.
The task of managing IT assets is very challenging as a business expands beyond a few distributed servers, workstations, laptops, tablets, and smartphones. It is even harder with devices that are heterogeneous, or that travel outside of the organization’s network. A key feature of the BigFix platform is that it is agnostic. While Windows still accounts for the majority of the operating systems powering laptop, desktops, and remote office servers, the rise of Bring Your Own Device (BYOD) has increased adoption of a whole new range of software. An effective endpoint management solution should comprehensively support multiple operating systems including Windows, MacOS, AIX, Unix, and Linux, whether physical or virtual.
Endpoints are highly vulnerable to attack and can represent significant risk including loss of control over the endpoint and the risk of losing valuable data. Many exposures are simply the result of endpoints that lack critical patches or have configuration errors that leave them open to attack and could be eliminated through the consistent application of configuration and update policies organization-wide.
Cybercrime prevention solutions protect web applications, computers, and mobile devices from online threats, such as advanced malware and phishing attacks including.
Advanced fraud protection prevents malware and phishing-driven fraud, detect account takeover attacks and fraudulent transactions and control mobile fraud risk.
Infrastructure protection breaks the cyber-attack chain at critical points with pre-emptive defense, securing employee endpoints from advanced information-stealing malware that can enable corporate system compromise.
Using BigFix you can
- Analyze vulnerabilities (patched or insecure configurations)
- Easily and automatically remediate all your networked systems
- Establish and enforce configuration policies across your network
- Distribute and update software packages
- View, modify, and audit properties of your networked client computers
- Install critical security patches on computers as soon as they’re made available by Microsoft, Apple, and other vendors.
- Asset inventory/discovery
- IT compliance reporting
- Software license management
- OS deployment
- Endpoint power consumption management
- Near real-time visibility into the state of endpoints
Addressing endpoint exposures is optimized when you deploy a single, unified solution that can identify all the endpoints, addresses the risks associated with security threats while also controlling cost, complexity, and IT staff burden while meeting compliance mandates.
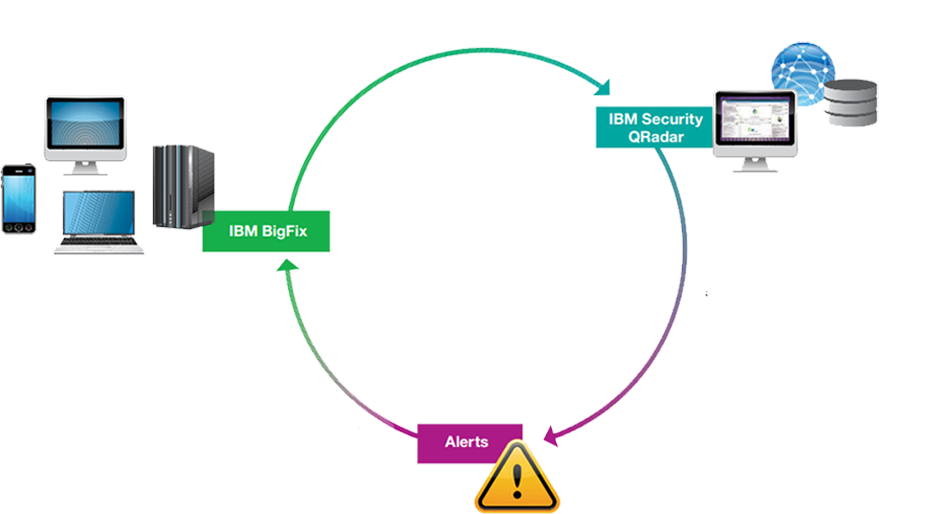
- BigFix is an agent-based software solution. Each computer communicates with the BigFix server to determine its status.
- Inventory information about the endpoint such as the presence or absence of critical security updates, IP address, operating system, and hardware data is collected. A complete list of all collected data is available.
- Easy Deployment and Management – The service can be installed in just days, across very large or highly distributed environments.
- BigFix provides Pervasive Visibility – distributed scanning and deep agent inspection makes it possible for you to see anything about any computer anywhere.
- The BigFix solution provides extremely specific ad-hoc queries which can be executed and answered across a globally distributed environment in minutes.
- You have the ability to secure, manage, and report on endpoints through any type of connection: On-site, Off-site, or public Internet.
- The BigFix agent and query language are optimized for near-invisible impact to network bandwidth and endpoint performance.
- Real-time Reporting with the agents who show any change in status, there is no need to initiate a new scan to know the current state of your assets.
How it works
- BigFix has two distinct components, a client, and a server. The client software is installed on computers that will be managed, while the server allows system administrators to monitor managed computers and enables patch deployment.
- The client provides information about the status, with respect to patching, of the machine it’s installed on. This information is conveyed to the main or root server, and allows administrators charged with managing BigFix clients to patch computers appropriately and as needed.
- Whenever a patch is released for a supported software, it is tested and packaged by IBM, then delivered to their customers generally within a matter of hours
Onexte Consulting is an IBM Business Partner that is specialized in implementing security solutions to a broad range of clients. Onexte has a comprehensive BigFix Lab that offers Implementation Support, Proof of Concept, Custom Development, Health Check Services, and Testing. Our BigFix team is staffed by certified professionals that specialize in all aspects of Endpoint Management. Our Architects and Engineers can work with you to ensure that you take full advantage of all of the potential that BigFix delivers. Our services include:
- Implementation on a complete end-to-end basis starting with assessment through deployment or only phases of the project as needed
- Training by certified experts in BigFix
- A full spectrum of low cost professional services options
- Audit confirmation to ensure all Endpoints are managed and all policies adhere to compliance and licensing agreements
Watch Video
Watch Video
Watch Video
Watch Video
Watch Video

IBM BigFix for Remote Control On Demand

Endpoint Management with IBM BigFix

BigFix Lifecycle – Multi OS Endpoint Management from a Single Console

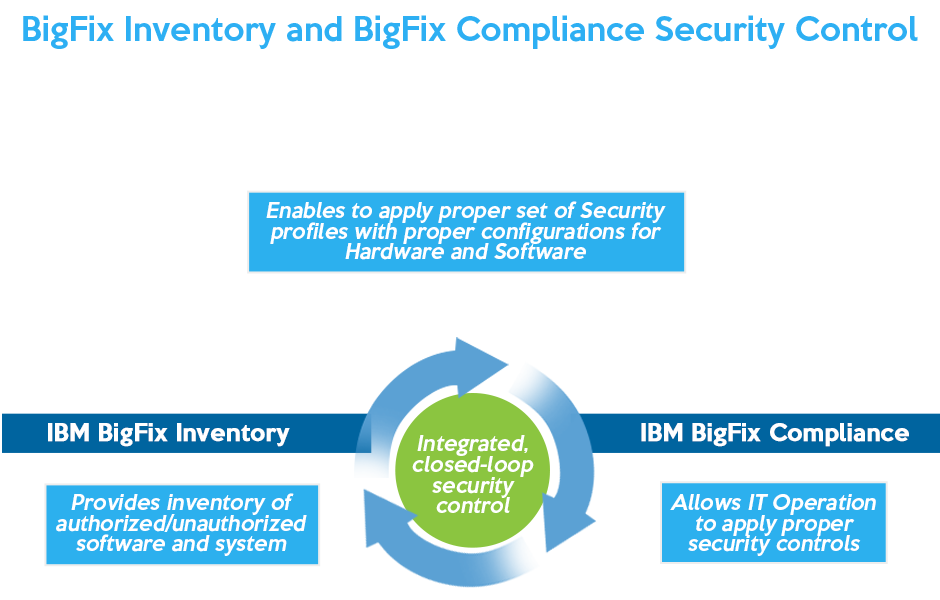
BigFix Inventory – Ensure Continuous Software Audit Compliance

BigFix Compliance – Continuous Endpoint Policy Enforcement