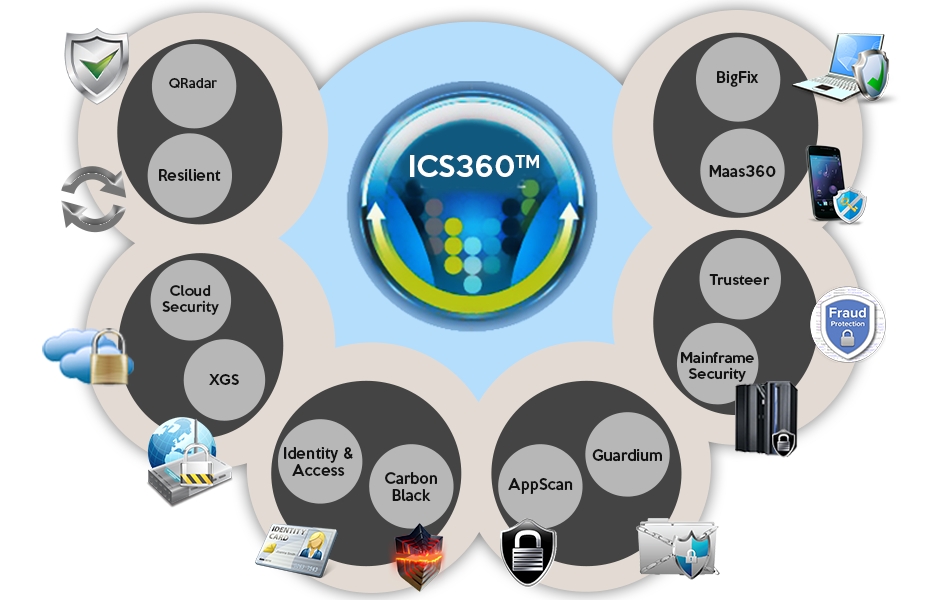
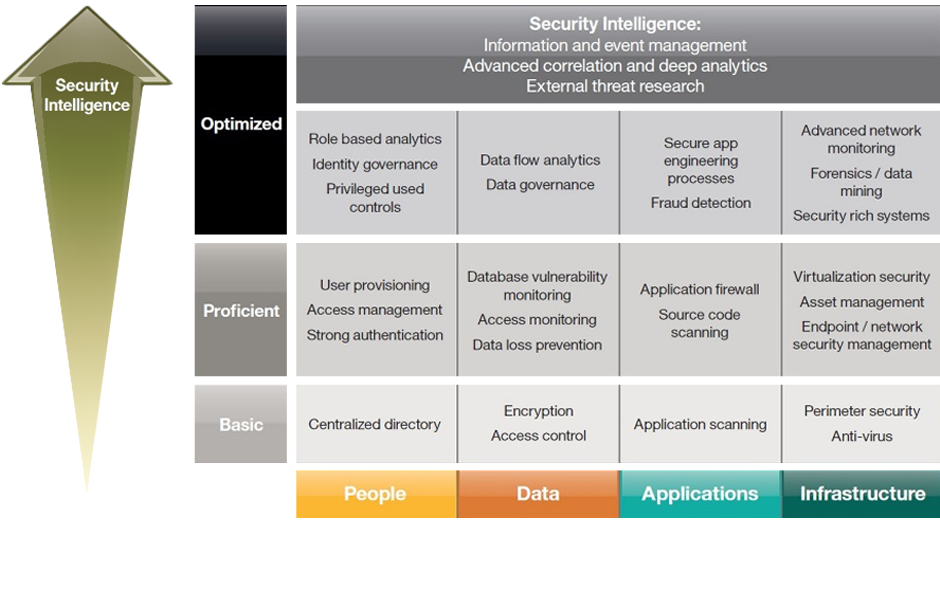
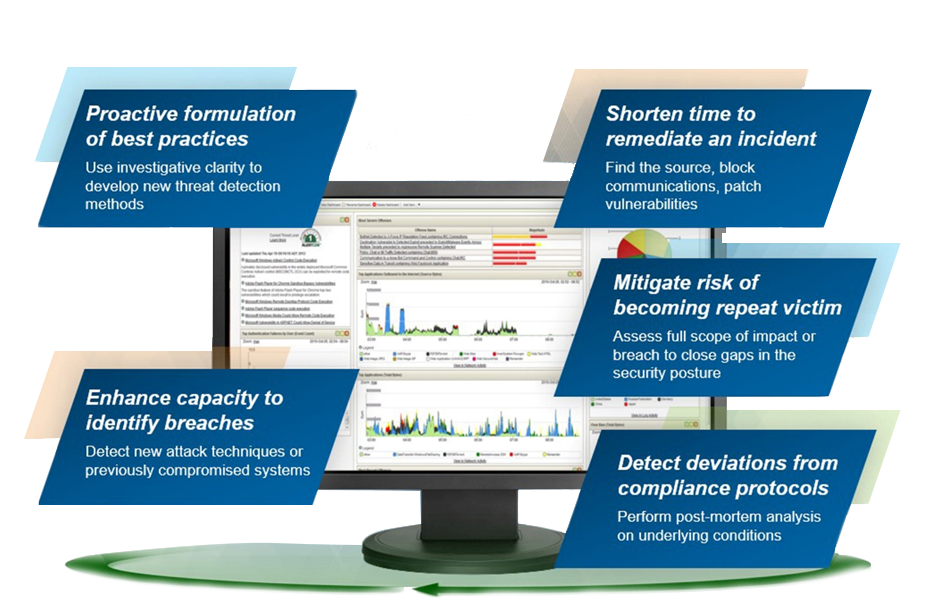
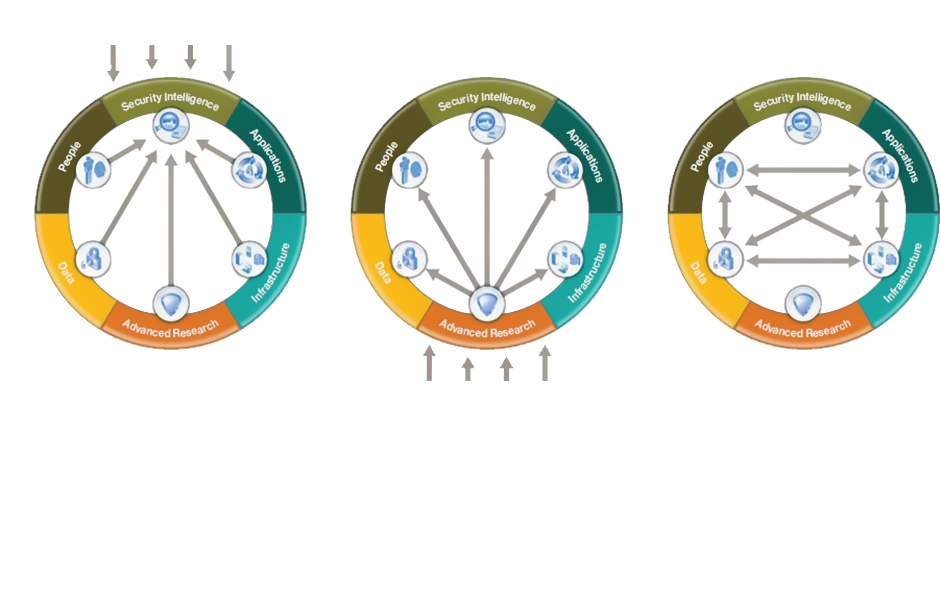
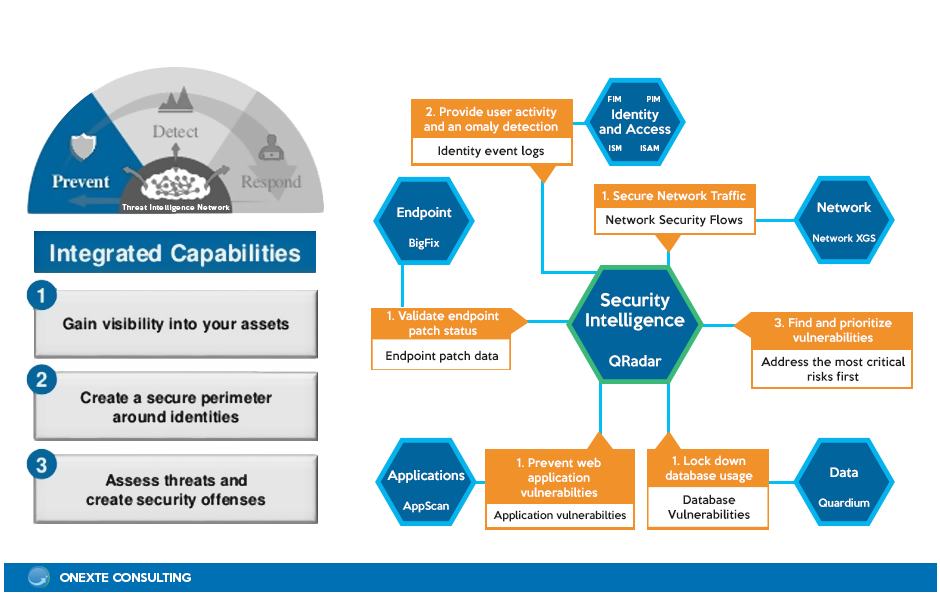
Protecting information confidentiality is a critical security objective for every organization. Starting with a good understanding of the business, an organization must weave IT security and IT risk management into the executive levels of business planning. IT security objectives must be defined for the organization as a whole and fall within the following categories: integrity, availability, confidentiality, use control and accountability. The objectives provide the criteria used to determine whether the architecture is appropriate for the given task. Our focus is on people, processes and technology, including benchmarking your IT security strategy and cost models.
In today’s world, IT departments need to ensure that the organization is in compliance with various industry and federal regulations (PCI, Sarbanes-Oxley, HIPAA) designed to keep sensitive customer data safe. An increasingly difficult task in today’s decentralized, mobile, app-filled world. Failure to meet rules and guidelines set by compliance standards could mean fines, penalties and loss of trust. But keeping the organization in compliance with industry and federal rules can be difficult, especially with more companies allowing workers to bring their own devices (BYOD). Low-tech methods like snooping, social-engineering or phishing are common techniques used by hackers against employees to gain unauthorized access to corporate information.
When security breaches make headlines, they tend to be about nefarious actors in another country or the catastrophic failure of technology. These kinds of stories are exciting to read and easier for the hacked company to admit to. But the reality is that no matter the size or the scope of a breach, usually it’s caused by an action, or failure, of someone inside the company. The role that insiders play in the vulnerability of all sizes of corporations is massive and growing, 60% of all attacks were carried out by insiders. Of these attacks, three-quarters involved malicious intent, and one-quarter involved inadvertent actors. Employees play a key role in protecting a company’s sensitive data. To overcome this threat, it’s important to educate all employees on different ways information can be acquired through very low-tech methods and give them tools they can use, like protecting corporate data displayed on a laptop with a privacy filter while traveling or how to recognize phishing attacks, to help mitigate any risk.
Having up-to-date security policies that are understandable to employees outside of IT is crucial. Information security policies should cover the creation, transmission, transport and retention of information; when and how information can be disposed of or removed from corporate servers/storage; remote, wireless, electronic and physical access to the corporate network; and security precautions to use while traveling.
Viruses and cybercriminals are constantly trying to hack into your private network and sensitive accounts. Just as you need a lock on your front door, you need digital locks that prevent unwelcome visitors from accessing confidential data such as credit card numbers, Social Security numbers or bank accounts. The IT security field integrates new technology that protects your computers and networks with consistency and vigilance.
Most organizations have weak controls in place to protect regulated data on mobile devices, and most employees, at one time or another, have circumvented or disabled required security settings on their mobile devices. Therefore, it is critical that preventive measures should be taken to restrict unauthorized access to corporate data should a mobile device be lost or stolen. Measures should be taken whether the device is enterprise-issued or not and should include:
- Enable devices and provide IT departments with the tools to perform a remote-wipe of sensitive data.
- Configure mobile devices so that only authorized applications can be downloaded and/or accessed on them.
- Invest in storage and data transmission encryption and other endpoint security tools.
- Prevent data storage and transmission to devices that lack adequate security clearance.
The primary challenge of IT security personnel is to balance the needs of users with the importance of protecting confidential data. Individuals, as well as organizations, have become incredibly reliant on the digital sphere in their daily operations. Technological advances mean that you can access personal emails on your phone in any location. The job of IT security professionals is to make sure that with your increased access comes increased security, and that you are still protected with each new breakthrough in technology. The biggest compliance-related issue facing CIOs today is shadow IT, a threat caused by the use of unseen third-party solutions including devices and apps.
Corporate IT has grown to be complex and cumbersome, so end users have started using their own third-party services to get their jobs done, such as large file sending services. But oftentimes these apps or solutions are out of the organization’s control, causing the IT department a major headache. The best medicine to cure the headache? Educate end users; give CIOs the controlled power to constantly assess services for suitability; and deploy modern enterprise solutions to solve overall compliance problems.
To ensure that sensitive data is being properly protected, choose a trusted service provider. Cloud services present significant benefits in terms of cost savings, scalability, flexibility. However, to ensure that your or your customer’s data is properly protected and in compliance with all relevant regulations, the vendor/service provider should meet all regulatory requirements.